Simplifying Cybersecurity for Small and Mid-Size Business

October is National Cybersecurity Awareness Month and we are participating in it by educating our community on basic cybersecurity practices.
The world of cybersecurity is complicated, especially for small and mid-sized business owners. To help you understand and simplify cybersecurity for your organization, we will use the National Institute of Standards and Technologies Cybersecurity Framework (NIST CSF) to focus on basic controls you can implement to protect your organization.
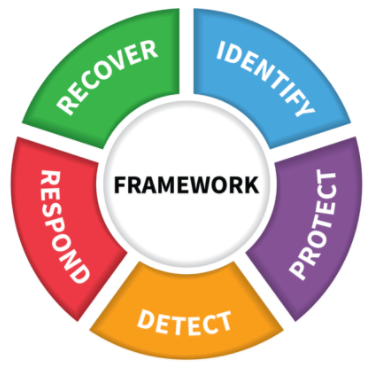
NIST CSF has five primary domains that seek to answer five questions to help you protect your business.
- Identify – Do we have a clear understanding of our requirements, our assets, and our risk?
- Protect – Are we protected from reasonably expected threats?
- Detect – Do we have appropriate situational awareness to detect a security incident?
- Respond – Do we have trained people and tested processes to respond to a security incident?
- Recover – Can we sustain the business operations if security incidents happen today?
Let’s look deeper at each of the domains and associated security controls.
Identifying Risk. Do you have a clear understanding of your regulatory, contractual and compliance requirements? Do you know what digital assets you need to protect (i.e., computers, applications, data)? Here are the minimum controls you should consider:
- Run an annual risk assessment to understand your risk. You can do this with your internal team or external help.
- Put technology and security policies in place and let your employees know what management’s expectations are and everyone’s roles and responsibilities.
- Understand who your critical vendors are and what type of access to your data and assets they have.
Protecting your Assets. A complex area due to the number of cybersecurity technologies and controls. During the COVID-19 practice, we started practicing some “hygiene controls” that had always been available but we never paid attention to, such as maintaining distance from one another or washing our hands thoroughly. These basic controls were complimented by others that also became “basic” quickly, such as using a face mask. Likewise, the term cyber-hygiene is used in technology to help people understand that basic controls to protect sensitive data and assets should be in place. Here are a few:
- Protecting your Identity/Access. Everyone has two items: a user ID and a password. Here are a few low costs controls to protect your identity:
- Use long passwords. Use passphrases such as My-dad-is-a-Legend-1959 (and it is complex and easy to remember)
- Use Multifactor Authentication (MFA). MFA is the combination of at least two different things:
- Something that you know (password)
- Something that you have (like a code received via text)
- Something that you are (fingerprint or face recognition)
- Use different passwords for your accounts
- Use a Password Manager App – so you only need to remember the master password to the App, and all your passwords are stored and encrypted in it
- Enable Automatic Updates. Everyone also has computers and mobile devices and uses software; update them! In addition, most operating systems like Windows or Apple can be automatically updated for new security patches. Turning this feature on will get the latest updates as vendors deploy them.
- Backup your Data. This is critical, and we will cover it later.
- Training Staff on Cybersecurity. You should regularly train your staff about cyber risk issues to ensure they are aware of enterprise cybersecurity policies and procedures and their role in protecting your company. Make security part of your next staff meeting by guiding a discussion on the topic or bringing a Security Specialist to help you.
Detecting Threats. If you’re a small business, you should do two things.
- Have a Managed Security Service Provider (MSSP) that is constantly looking at your infrastructure and data and trying to detect if there are unauthorized access or anomalies
- If you already have an MSSP, then ask them what they are doing to monitor your environment
Responding to a Cybersecurity Incident. A cybersecurity incident is going to hit your business at some point. Thus, you are responsible for having a plan so everyone knows what actions must be taken when something happens.
- Document your Incident Response Plan, which should include roles and responsibilities; how to report an incident; who the first responders are; who communicates; and more.
- Test your plan yearly. Have a conversation with your critical staff and discuss a scenario to go through your plan. This is known as a tabletop exercise.
Recovering from an Incident. If that incident happens, can you recover from it? If, for example, you are hit with Ransomware, will you pay the ransom?
- Can you restore your data from backups? Earlier I mentioned that data backups are critical to your business. This is due to the emergence of Ransomware, an attack combined with an extorsion that seeks to encrypt your data first, to then ask you to pay a ransom to get it back. If your data is encrypted, having a backup can help you recover it and avoid paying extortionists.
- Have a Disaster Recovery and Business Continuity Plan to continue running critical business operations when a significant incident disrupts normal operations.
- Finally, you protect you most important assets and family with different type of insurance policies that you never want to use. One of those assets is your business; therefore, acquiring a Cyber Liability Insurance Policy is an important protection to have. Know that the insurance carriers are asking for most of these controls to be in place when they are underwriting your policy; another reason to implement them.
When building a cybersecurity program, seek to answer these five critical questions: 1) do I understand my risk? 2) are we reasonably protected from threats? 3) Do we have situational awareness of our environment? 4) do we have processes to respond to a security incident? And 5) can we sustain critical business operations? By answering these questions and implementing some basic hygiene security controls, you can protect your business without having to boil the ocean.